Demystifying Proxy Servers: How They Direct and Secure Your Web Traffic
Welcome to my new blog series that delves into the fascinating world of proxy servers. As internet users, we interact with proxy servers on a daily basis, yet many of us may not fully understand what they are and how they shape our online experiences. In this post, I aim to demystify proxy servers by providing a comprehensive overview of their functionality, benefits, and use cases. Whether you're an individual seeking to enhance your online privacy or an organization looking to optimize web traffic, understanding proxy servers is key. Join me as I unravel the workings of proxy servers, explore their various types, highlight their features and benefits, and even touch upon their synergy with Web Proxy Auto-Configuration (PAC) files. By the end of this series, you'll have a solid grasp of how proxy servers direct and secure your web traffic, empowering you to make informed decisions about their implementation. Let's get started!
What is a Proxy Server?
Proxy servers provide a wide variety of functionality when implemented correctly by an enterprise. At its most basic, a proxy server acts as an intermediary between a client and a web server, facilitating requests and responses on behalf of the client. It can enhance security, improve performance, provide anonymity, and offer various other functionalities to optimize web traffic. While the breadth and depth of this functionality is quite wide, I believe that proxy servers can be said to serve two primary goals; to increase security, and to improve performance optimization. I will use these two goals to further break down the component functionality of proxy servers as we continue this discussion. The first area I'd like to focus on are the capabilities of proxy servers that help improve overall security posture.
Proxy Server Security Capabilities
As I'm writing this post I find myself thinking that if I list out the security capabilities that can be achieved by leveraging a proxy server and explain each of them in-depth, we'll probably still be here next week reading through a novel of capabilities. Because of that, I'm going to bullet out some of these capabilities with a quick explanation and come back to these topics and write individual posts on the capabilities that merit their own. When I write those posts I will come back and link from this article to those others. So, with all of that being said, I've listed out what I believe to be the core security capabilities that can be achieved by leveraging a proxy server.
- Access Control and Filtering: Proxy servers can enforce access control policies by filtering and blocking access to specific websites, content categories, or URLs. This helps prevent users from accessing malicious or inappropriate content.
- Firewall Protection: Proxy servers can act as a firewall, monitoring and controlling incoming and outgoing traffic based on predefined rules. This helps detect and block unauthorized access attempts, malware, and other threats.
- SSL/TLS Encryption and Decryption: Proxy servers can handle SSL/TLS encryption and decryption on behalf of clients, providing an additional layer of security. This helps protect sensitive information by encrypting the communication between the client and the web server. In addition, this also allows a correctly configured proxy server to inspect traffic that has been encrypted with TLS providing more visibility into the network traffic to ensure malicious content is not present.
- Intrusion Detection and Prevention: Proxy servers can analyze web traffic for suspicious patterns or malicious activities, helping to detect and prevent intrusion attempts, malware infections, and other security threats.
- Data Loss Prevention: In tandem with SSL / TLS inspection, proxy servers can monitor and prevent the unauthorized transmission of sensitive or confidential data, helping to mitigate the risk of data breaches and leaks.
- Anonymous Browsing: By masking the client's IP address, proxy servers can provide a level of anonymity, making it harder for websites to track and identify users. It is important to note, however, that simply leveraging a proxy server does not inherently mask or anonymize user traffic.
- DDoS Mitigation: Proxy servers can help mitigate Distributed Denial of Service (DDoS) attacks by filtering and absorbing malicious traffic before it reaches the web servers, thus preventing service disruptions.
- Web Application Firewall (WAF): Proxy servers can include Web Application Firewall capabilities to protect web applications from common vulnerabilities, such as SQL injection, cross-site scripting (XSS), and more.
All of these capabilities can be leveraged in different ways depending on the proxy server infrastructure that is implemented by an organization, and not all proxy servers are capable of all of the security functionality listed above. That being said, this should provide you with a solid overview of the security capabilities which can be achieved through implementing proxy server infrastructure. The next section will discuss the performance optimization benefits that proxy servers can provide to an organization.
Proxy Server Performance Optimization Capabilities
As noted with the security capabilities above, not all proxy servers are created equal. While benefits and capabilities can be mixed and matched depending on the infrastructure and the implementation, typically an organization will also use a subset of point products to achieve a specific goal and many of these point products fall into the category of performance optimization. Through leveraging proxy servers, organizations can recognize the benefits listed below to help optimize the performance of their network traffic across the organization.
- Caching: The caching capability of a proxy server allows it to store and serve frequently accessed web content from its cache. This reduces the load on the web server and speeds up the delivery of content to clients.
- Load Balancing: By distributing client requests across multiple web servers, a proxy server helps balance the load and ensures optimal utilization of server resources. This improves performance, scalability, and availability of web services.
- Protocol Conversion: Proxy servers can facilitate protocol translation, allowing clients and servers using different protocols to communicate with each other. This enables seamless integration and interoperability between different systems and protocols.
- Content Compression: Proxy servers can compress web content before delivering it to clients, reducing the amount of data transmitted over the network. This minimizes bandwidth usage and improves page load times, particularly for clients with slower internet connections.
- Content Filtering and Categorization: Proxy servers can analyze and categorize web content based on predefined rules and policies. This categorization allows for more efficient content filtering, access control, and enforcement of internet usage policies within an organization.
- Content Modification: Proxy servers can modify web content on the fly. For example, they can inject advertisements, remove unwanted elements, or rewrite URLs to ensure compatibility with client systems or security requirements.
Now that I've given a quick overview of the benefits of using proxy servers, and a quick definition, let's spend some time talking about how they actually work.
How do Proxy Servers Work?
At the most basic level, when a web browser requests a resource from a web server there is a handshake that takes place in the TCP/IP stack to facilitate that communication. The role of a proxy server is to intercept that traffic in the middle, perform whatever actions it is configured to perform and then forward that traffic on to its final destination. The image below illustrates very simply where the proxy server sits in this communication stream.
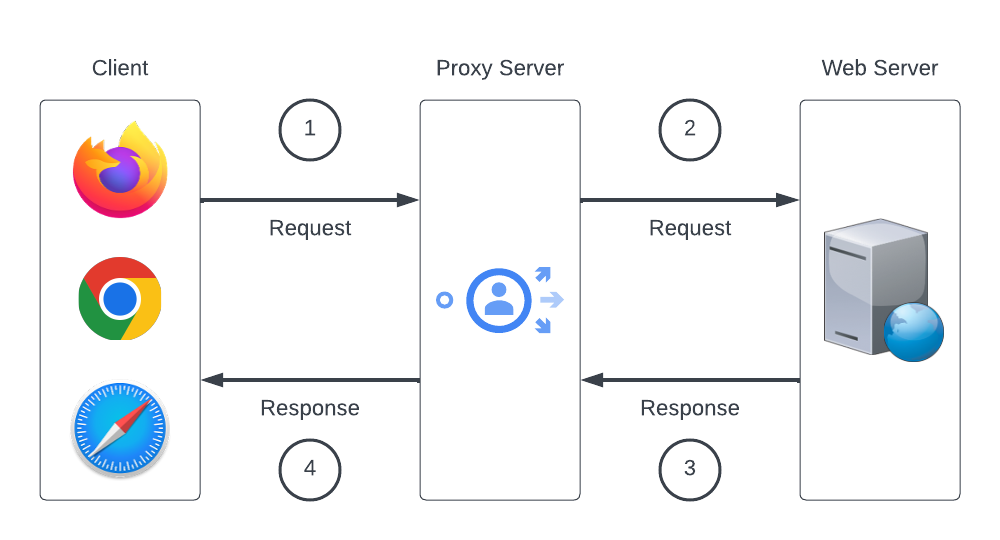
It's crucial at this point of the post that I stop briefly and explain that there are two primary types of proxy architecture; explicit proxy and transparent proxy. I'll briefly define each before we move on.
Yes, that is an accurate statement. In the context of proxy architectures, two common types are explicit proxy and transparent proxy. Let's briefly define each:
- Explicit Proxy: In an explicit proxy architecture, the client's web browser or application is explicitly configured to use the proxy server. This can be done in a variety of ways, but see my series on PAC files for some examples. The client's network settings or application configuration specifically designate the proxy server's IP address and port number. When the client wants to access a web resource, it sends the request to the proxy server explicitly.
- Transparent Proxy: In a transparent proxy architecture, the proxy server is deployed in such a way that the client is unaware of its presence. The proxy server intercepts the client's web traffic transparently, without the need for any explicit configuration on the client side. The client's requests are automatically redirected to the proxy server by network infrastructure or firewall rules.
These two types of proxy architectures differ in terms of how the client interacts with the proxy server. In an explicit proxy, the client is explicitly aware of and configured to use the proxy server. In a transparent proxy, the client is unaware and doesn't require explicit configuration, as the proxy interception is handled transparently by the network infrastructure or firewall.
Each type has its advantages and considerations. Explicit proxies provide more control and flexibility, allowing clients to choose whether and how to use the proxy. Transparent proxies, on the other hand, can be easier to deploy and manage in certain network environments but may have limitations in terms of client control and configurability.
The example image above that illustrates the four steps of the conversation would be an example of an explicit proxy architecture because the client is sending its traffic (during step 1) directly to the proxy server. The image below, in contrast, would be an example of a transparent proxy architecture. From the client's perspective, the traffic is being sent directly to the web server, and from the web server's perspective, it is returning the traffic directly to the client. However, based on network conditions / configuration, the traffic is actually being re-routed to a proxy server during the course of that communication.
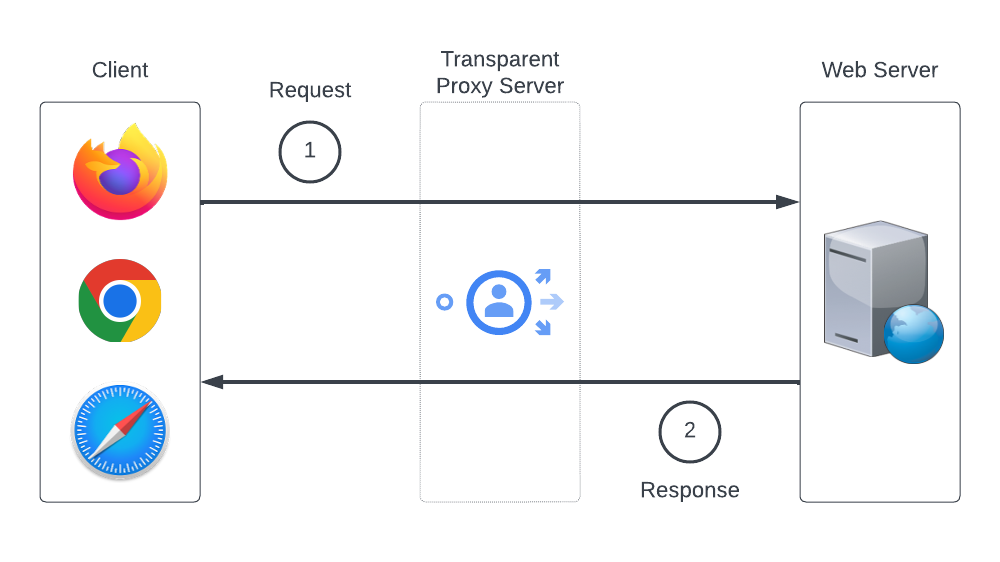
Without going into a crazy amount of technical depth, this is how a proxy server functions and should give you the level of understanding required to follow the rest of this post. Let's move on and discuss a few different types of proxy servers and their functions.
Types of Proxy Servers
There are quite a few different types of proxy servers that exist out in the wild. I'll list them and a brief explanation below but for the purposes of this post, we're going to focus on the three most common types; forward proxy, reverse proxy and transparent proxy. As you have probably guessed from that, a transparent proxy is utilized when the proxy server infrastructure is built in a transparent architecture, like we discussed above. Briefly, let's take a look at what these three types of proxy servers accomplish:
- Forward Proxy: A forward proxy server acts on behalf of clients to access resources from the internet. When a client requests a web resource, it sends the request to the forward proxy server, which then retrieves the resource from the internet and forwards it back to the client. The client is aware of and explicitly configured to use the forward proxy. Forward proxies are commonly used for functions like caching, content filtering, and anonymizing client requests. This type of proxy server is deployed when an explicit proxy architecture is in use.
- Reverse Proxy: A reverse proxy server operates on behalf of web servers to handle client requests. It sits between the clients and web servers, receiving requests from clients and forwarding them to the appropriate backend server. When the backend server responds, the reverse proxy server sends the response back to the client. Reverse proxies are often used to improve scalability, load balancing, security, and SSL/TLS termination for web applications.
- Transparent Proxy: A transparent proxy server intercepts client requests without requiring explicit configuration on the client side. It is typically deployed at the network level, intercepting and redirecting traffic transparently. The client is unaware that their requests are being proxied. Transparent proxies are often used for functions like content caching, content filtering, or network optimization without requiring client-side configuration. This type of proxy is deployed when a transparent proxy architecture is in use.
It's worth noting that the terms "forward proxy" and "reverse proxy" describe the direction of the proxying in relation to the client and server, respectively. As I indicated in the opening of this section, there are also quite a few types of proxy servers that provide specialized functionality. I'll list these and a brief description below, but we won't be diving any deeper into them during this article.
- Open Proxy: An open proxy server, also known as a public proxy or free proxy, is accessible to anyone on the internet. It allows users to route their web traffic through the proxy server without any authentication or restrictions. Open proxies can be used to bypass censorship, access geographically restricted content, or hide one's identity. However, they can also pose security risks and may be abused for malicious activities.
- Load Balancing Proxy: Load balancing proxies distribute incoming client requests across multiple backend servers to achieve load balancing and improve performance. They can evenly distribute the traffic based on different algorithms, such as round-robin, least connections, or weighted distribution. Load balancing proxies help optimize resource utilization and ensure high availability of services.
- SSL/TLS Proxy: SSL/TLS proxies, also known as SSL/TLS terminators or SSL/TLS offloaders, handle SSL/TLS encryption and decryption on behalf of backend servers. They can relieve the computational burden of SSL/TLS processing from the backend servers, improving their performance. SSL/TLS proxies also allow for centralized management and inspection of encrypted traffic.
- DNS Proxy: A DNS proxy server intercepts DNS (Domain Name System) requests from clients and resolves them on behalf of the client. It helps improve performance by caching DNS responses and reducing the latency of DNS lookups. DNS proxies can also provide additional functionalities like content filtering, blocking malicious domains, or enforcing DNS-based policies.
- Application-Level Proxy: Application-level proxies, also known as application gateways or application layer proxies, operate at the application layer of the network stack. They provide advanced application-specific functionalities and security features. Application-level proxies are often used for protocols such as HTTP, FTP, SMTP, or SIP, allowing deep inspection, content modification, and policy enforcement.
Thanks for reading through this post. We covered a basic introduction to what proxy servers are, the benefits they can provide - at a high level - and the most common types of proxy servers. In the next post of this series we will dive a little deeper into the technical functionality behind a proxy server, more technical detail on the benefits we discussed above, the relationship between Proxy Auto-Configuration (PAC) files and some best practices for proxy server deployment. As always, leave a comment if you want to and check back for the next post!